November Web3 Security Incident Review: Total Loss Approximately $86.24 Million
In November 2024, there were 21 hacking incidents, resulting in losses of approximately $76.86 million, with $25.5 million recovered. The causes of the incidents included contract vulnerabilities, account hacks, and price manipulation, among others. Additionally, there were 9,208 victims of phishing incidents this month, with losses amounting to $9.38 million.
Author: SlowMist Security Team
Overview
In November 2024, the total loss from Web3 security incidents was approximately $86.24 million. Among these, according to the SlowMist Blockchain Hacked Archive (https://hacked.slowmist.io), there were 21 hacking incidents resulting in losses of about $76.86 million, with $25.5 million recovered. The causes of these incidents included contract vulnerabilities, account hacks, and price manipulation. Additionally, according to the Web3 anti-fraud platform Scam Sniffer, there were 9,208 phishing incident victims this month, with losses amounting to $9.38 million.

(https://dune.com/scam-sniffer/november-scam-sniffer-2024-phishing-report)
Major Security Incidents

MetaWin
On November 4, 2024, according to on-chain detective ZachXBT, the crypto gambling platform MetaWin was allegedly attacked, resulting in the theft of over $4 million on the Ethereum and Solana chains. MetaWin CEO Skel stated that the attacker exploited the platform's frictionless withdrawal system to breach MetaWin's hot wallet.

DeltaPrime
On November 11, 2024, the DeFi protocol DeltaPrime was attacked on Avalanche and Arbitrum, with initial loss estimates of $4.75 million. The root cause of this attack was the lack of input validation in the reward claiming feature.

(https://x.com/DeltaPrimeDefi/status/1855899502944903195)
Thala
On November 15, 2024, the Aptos-based DeFi project Thala was attacked, resulting in the theft of $25.5 million, with the attacker exploiting a vulnerability in its smart contract. The project team suspended the related smart contracts and froze some tokens, ultimately successfully freezing about $11.5 million in assets. After collaborating with law enforcement and several blockchain security teams, the project team successfully negotiated to recover the assets, allowing the attacker to keep $300,000 as a bounty.

(https://x.com/thalalabs/status/1857703541089120541?s=46\&t=bcMyidYO0QkS5ajIW9CBdg)
DEXX
On November 16, 2024, multiple users' funds on the on-chain trading terminal DEXX were stolen. According to the SlowMist Security Team, the losses from this incident have reached $21 million. Currently, the SlowMist Security Team is assisting DEXX officials and partners in ongoing analysis. On November 28, the SlowMist Security Team announced that they had collected 8,612 DEXX attacker addresses on the Solana chain, with EVM chain attacker addresses to be disclosed after the cleaning statistics are completed.

(https://x.com/MistTrack_io/status/1862134946090881368)
Polter Finance
On November 17, 2024, the Fantom-based DeFi project Polter Finance was attacked, resulting in losses of approximately $12 million. The attacker drained the BOO token reserves through a flash loan, artificially inflating the calculated price of BOO. This allowed them to borrow tokens far exceeding the actual value of the collateral, resulting in substantial profits. The platform's founder stated that they have reported to the Singapore authorities and attempted to contact the attacker through on-chain messages to negotiate the return of funds but have not yet received a response.

(https://x.com/polterfinance/status/1857971122043551898)
Feature Analysis and Security Recommendations
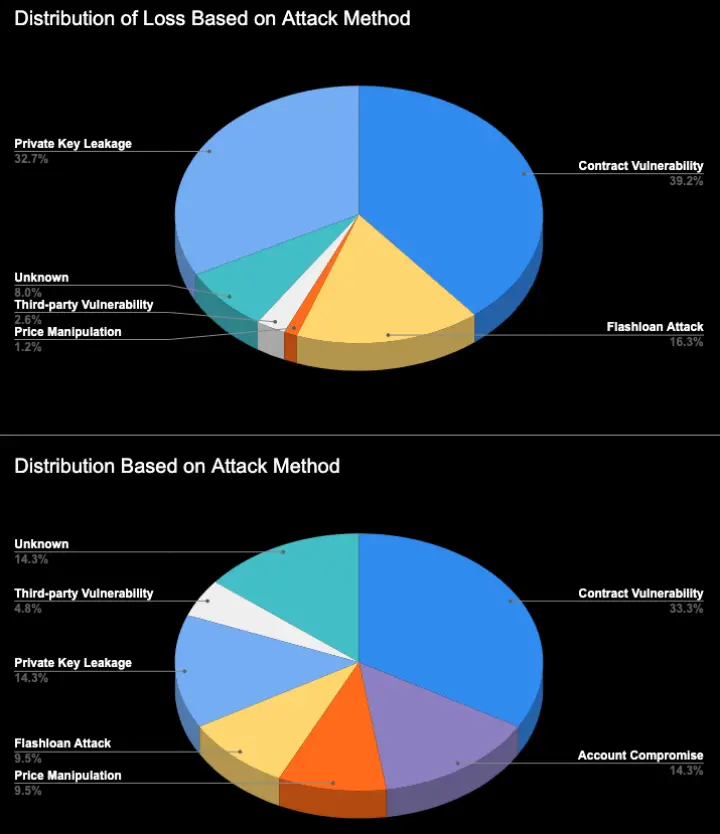
The number of security incidents and the scale of losses this month have significantly decreased compared to last month, reflecting ongoing improvements in security measures within the industry. Notably, contract vulnerabilities remain the highest proportion in terms of both the distribution of attack causes and the scale of losses. The seven incidents of contract vulnerability exploitation this month resulted in losses of approximately $30 million, accounting for 39% of total losses. The SlowMist Security Team advises project teams to remain vigilant and conduct regular comprehensive security audits, track and address new security threats and vulnerabilities to protect project and asset security.
Additionally, the SlowMist Security Team noted that there were real cases of AI poisoning attacks targeting the crypto industry this month. This phenomenon indicates that the target range of supply chain attacks is further expanding. Some developers, in pursuit of efficiency, may overly rely on AI-generated code while neglecting the review of code security. Therefore, the SlowMist Security Team reminds developers and project teams not to blindly trust the output results when using AI-generated code. All code should undergo rigorous security audits and testing before being put into actual use to prevent security risks and protect the project and users' assets. Meanwhile, project teams should strengthen overall supply chain security management, conduct comprehensive assessments of third-party tools and services, and continuously monitor security dynamics in related fields to respond promptly to new threats.
Disclaimer: The content of this article solely reflects the author's opinion and does not represent the platform in any capacity. This article is not intended to serve as a reference for making investment decisions.
You may also like
Solana’s DeFi Growth Could Challenge Ethereum
Franklin Templeton highlights Solana’s rising DeFi activity, posing a challenge to Ethereum’s dominance in the sector.Ethereum’s Lead Faces New ChallengesThe Future of DeFi: Can Solana Surpass Ethereum?

Best Meme Coin to Buy Today: BTFD Coin’s $6.26M Presale Surge, Moo Deng’s Tax-Free Trading, and Turbo’s AI Experiment
Looking for the best meme coin to buy today? BTFD Coin crosses $6.26M in presale, Moo Deng’s no-tax model attracts traders, and Turbo’s AI-powered vision gains momentum.BTFD Coin’s Staking Rewards Give Investors the EdgeTurbo’s AI-Generated Concept Keeps the Community IntriguedFinal Thoughts

World Liberty Financial & SUI Unveil Strategic Token Reserve
World Liberty Financial partners with SUI to launch a Strategic SUI Reserve, enhancing liquidity and bridging traditional finance with blockchain technology.Why This Strategic Reserve MattersA Step Towards Mainstream Crypto Adoption

SUI Surges 13.7% on World Liberty Financial Partnership
SUI price jumps 13.7% after announcing a strategic partnership with World Liberty Financial. Who's next to join forces?Expanding Blockchain Financial ServicesWhat’s Next?

